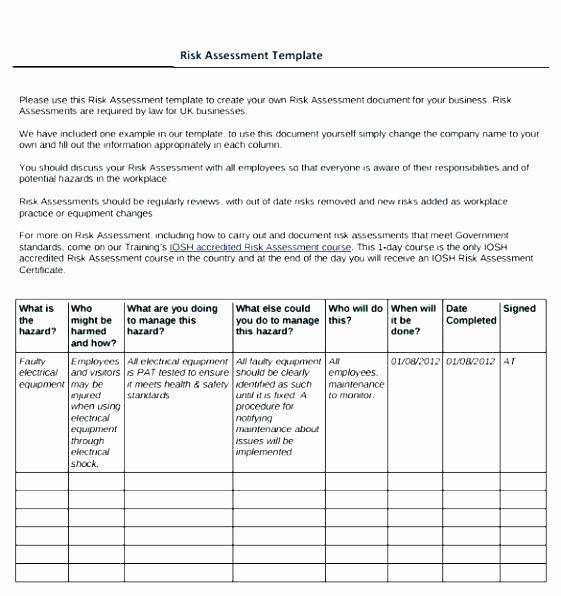
Written Information Security Program Template

Our objective in the development and implementation of this written information security plan is to create effective administrative technical and physical safeguards in order to protect our customers non public personal information.
Written information security program template. Our list includes policy templates for acceptable use policy data breach response policy password protection policy and more. Sans has developed a set of information security policy templates. Elimination of potential legal liabilities. This article outlines an incremental approach to rolling out an information security program.
But it s important to understand how your policy will fit into a greater security strategy. The inappropriate use of the resources of the organization. A well written security policy should serve as a valuable document of. A solid policy is built with straightforward rules standards and agreements that conform to industry best practices and regulatory requirements.
The prevention of wastes. This iso based wisp is a comprehensive customizable easily implemented microsoft word document that contains the iso 27002 based policies control objectives. An incremental approach to building an information security program. The written information security program wisp is updated as needed and at least annually by the director of information security section 3.
A standard document model written information security program wisp addressing the requirements of massachusetts s data security regulation and the gramm leach bliley act glba safeguards rule. These are free to use and fully customizable to your company s it security practices. Including laptops and portable devices that contain personal information. Refer to appendix a.
Available resources for a template to complete the information classification activity. A good information security policy template should address these concerns. Sample written information security plan i. Its scope is a bit wider than just writing an information security policy itself.
It contains cybersecurity policies and standards that align with nist 800 53 including nist 800 171 requirements. The protection of the valuable information of the organization. Additionally a sample is provided. This version of the written information security program wisp is based on the nist 800 53 rev4 framework.
Information classification documents can be included within or as an attachment to the information security plan. This standard document provides general guidance for developing a wisp as may be required by other state and federal laws and best practices. The iso version of the written information security program wisp is a comprehensive set of it security policies and standards that is based on theiso 27002 2013 framework and it can help your organization become iso 27002 compliant.